Amnext Lottery - Smart Contract Audit Report
Summary
 The Amnext has built a series of contracts to enable users to participate in lotteries.
The Amnext has built a series of contracts to enable users to participate in lotteries.
We reviewed a series of Amnext's Lottery contracts using code provided to us by the team. For this audit, we reviewed the following contracts:
Notes on the Contracts:
- The Prize Pool Factory contracts (Venus, Pancake, and AMC) are designed to allow for the deployment multiple lottery pools.
- When a new pool is created, a copy of the base PrizePool contracts is deployed
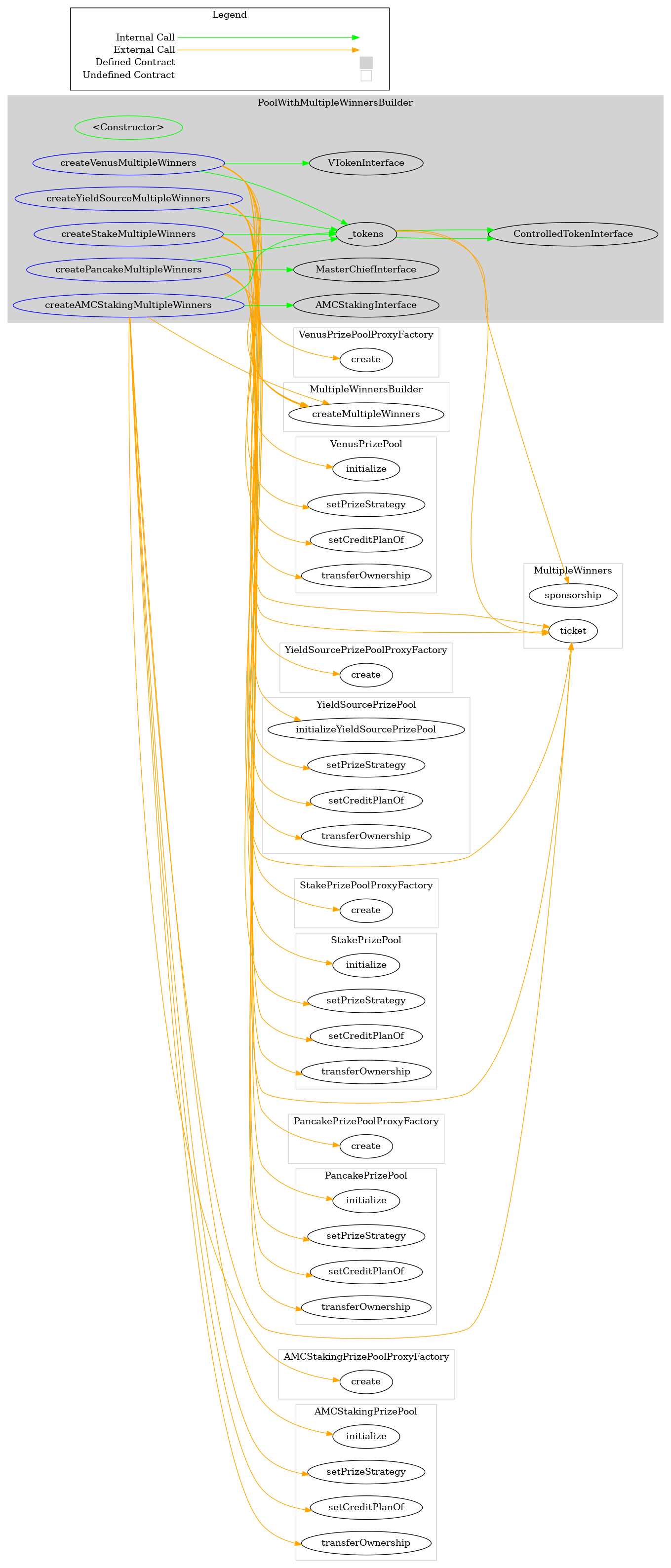
- The PoolWithMultipleWinnersBuilder contract is a variant of the Factory contracts, with additional logic to support the deployment of lottery pools with multiple winners.
- Users can enter into the Lifetime Lottery by depositing an ERC20 token; though they must register first.
- After registering users can buy 'levels' in the Lifetime Lottery by paying to the contract. (This is currently commented-out for testing but ought to be re-enabled prior to deployment).
- Users who refer other users to buy levels in the contract will receive rewards for their referrals in the form of both AMC tokens and staked AMC tokens. Two levels for referrals exist.
- The team will set values used in the lottery upon deployment. No ownership-restricted functions are present, so once deployed the contract's key variables cannot be altered.
- A price calculation is used to get the USDT price of the AMC token. While this method is somewhat suseptible to flash loans, the value that can be extracted will be below the cost of taking a flash loan; so this implementation is acceptable.
- In all of the xxxxPrizePool contracts, the initialize() can be declared external instead of public to save some gas when called.
- The _supply() and _redeem() functions in the xxxxPrizePool contracts perform redundant logic in defining assetToken. It instead could be defined globally to save some execution cost.
- The returning of the 'diff' value in the _redeem() function in the xxxxPrizePool contracts could be streamlined to save on gas.
- SafeMath is utilized across all contracts to prevent overflows.
Audit Findings Summary:
- No security issues from outside attackers were identified.
- Ensure trust in the team as they have notable control in the ecosystem.
- Date: June 4th, 2021.
External Threat Results
| Vulnerability Category | Notes | Result |
|---|---|---|
| Arbitrary Storage Write | N/A | PASS |
| Arbitrary Jump | N/A | PASS |
| Delegate Call to Untrusted Contract | N/A | PASS |
| Dependence on Predictable Variables | N/A | PASS |
| Deprecated Opcodes | N/A | PASS |
| Ether Thief | N/A | PASS |
| Exceptions | N/A | PASS |
| External Calls | N/A | PASS |
| Integer Over/Underflow | N/A | PASS |
| Multiple Sends | N/A | PASS |
| Suicide | N/A | PASS |
| State Change External Calls | N/A | Pass |
| Unchecked Retval | N/A | PASS |
| User Supplied Assertion | N/A | PASS |
| Critical Solidity Compiler | N/A | PASS |
| Overall Contract Safety | PASS |
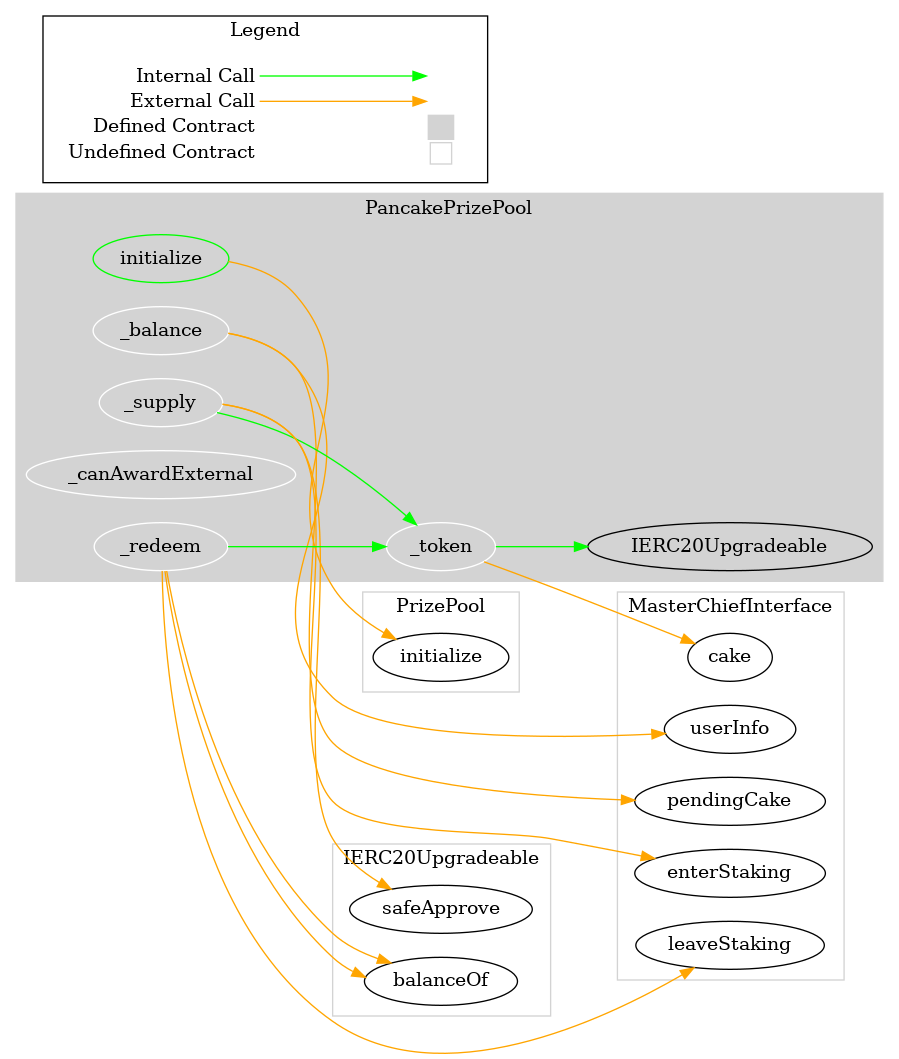
Visualizations: Pancakeswap Lottery


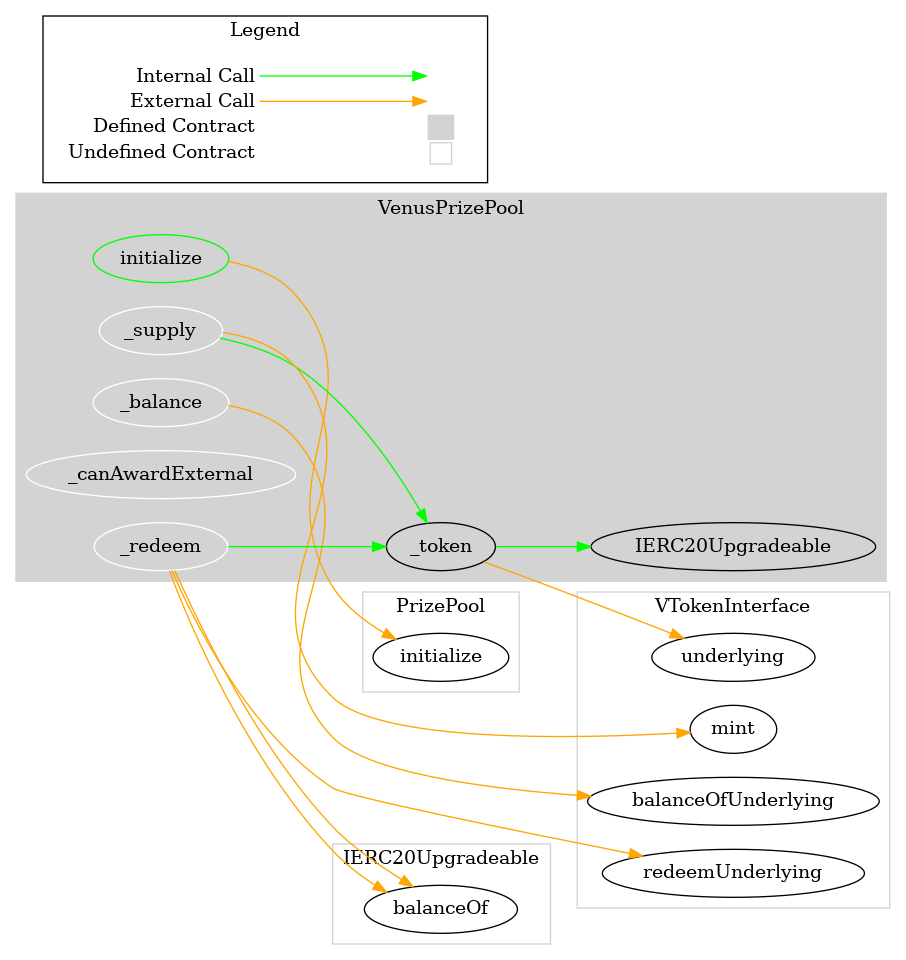
Visualizations: Venus Lottery
Visualizations: AMCStakingPrizePool

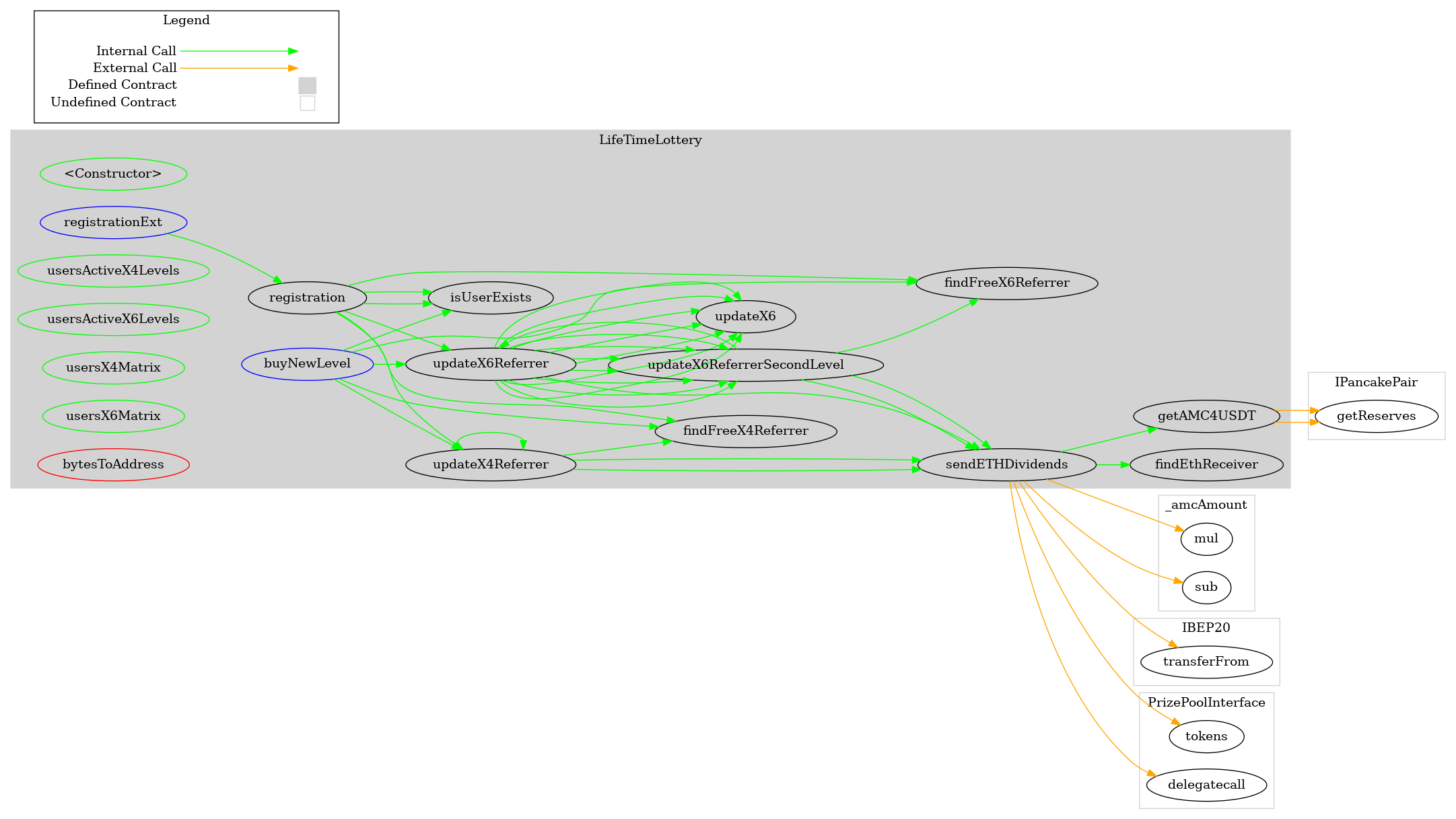
Visualizations: LifeTimeLottery

Visualizations: PoolWithMultipleWinnersBuilder