Lodestar Finance
Smart Contract Analysis
Audit Summary
 Lodestar Finance is a lending platform that allows users to deposit collateral for l-tokens. Users may then borrow other tokens based on their collateral deposited.
Lodestar Finance is a lending platform that allows users to deposit collateral for l-tokens. Users may then borrow other tokens based on their collateral deposited.
This analysis will mainly focus on the transaction during block 45121904 on the Arbitrum Mainnet.
Overview
Date: December 13th, 2022.
On December 10, 2022, Lodestar Finance experienced an exploit involving their lUSDC token at 0x5e3f2abaecb51a182f05b4b7c0f7a5da1942de90 and lplvGLP token at 0xcc25dac54a1a62061b596fd3baf7d454f34c56ff. The attack utilized an 8-figure flashloan that allowed the initial attacker and several copycat attackers to drain liquidity from the entire protocol.
Analysis
- Two addresses were used to leverage the exploit. The first attacker (A) is an unverified contract at 0x7596acadf6c93f01b877f5a44b49407fffc53508 and the second (B) is another unverified contract at 0xe1ba6511f95d8e6bca786ecbc4472de4c4137bff.
- A begins the exploit by accumulating 70,096,512.99 USDC through various flashloans.
- The USDC is all deposited into the Lodestar lUSDC contract where A is minted 3,490,966,280.82 lUSDC tokens in return.
- The deposited USDC is used as collateral throughout the rest of the exploit.
- A then borrows the lplvGLP contract's entire underlying plvGLP balance of 3,814,441.16 tokens.
- These tokens are then immediately deposited back into the lplvGLP contract for 190,691,885.01 lplvGLP tokens.
- A has enough collateral to repeat this process 16 times. The result is 3,051,070,160.01 lplvGLP tokens.
- A has leveraged their initial USDC flashloan for as much lplvGLP as possible through the iterative borrow-deposit-mint process.
- The protocol allows this as the current value of the lplvGLP tokens is covered by the amount of USDC that A initially deposited.
- Manipulation of the value of plvGLP token in the PriceOracleProxyETH contract allows the user to inflate the value of their leveraged lplvGLP tokens.
- We can see in the PriceOracleProxyETH contract, that the plvGLP price is determined from a ratio of the calculated exchange rate and glp Price:
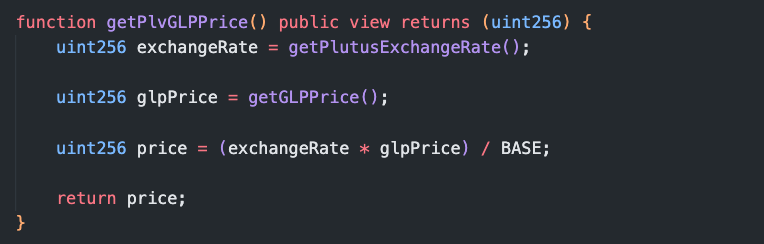
- Looking at the getPlutusExchangeRate() function, we can see the exchange rate is determined based on the ratio of assets in the plvGLP contract to the total supply of plvGLP tokens:
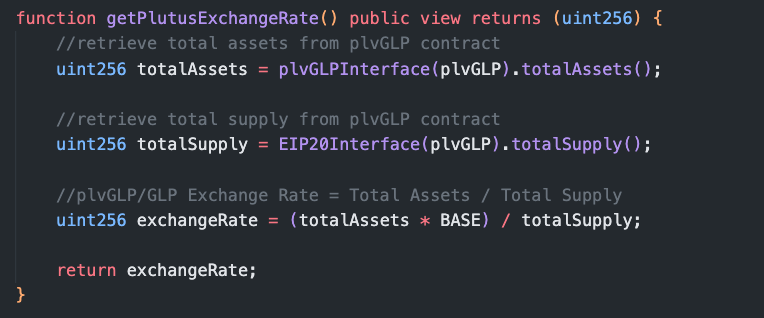
- The initial amount of plvGLP tokens A was able to borrow was based on this ratio when the exploit started.
- A is able to manipulate this value through the GlpDepositor donate() function:
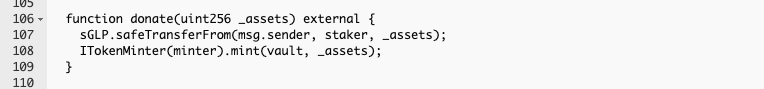
- This function increases the amount of assets in the plvGLP contract without increasing the total supply of tokens. This is the correct behavior for the plvGLP contract but is exploited by A in the PriceOracleProxyETH contract.
- The amount of assets any user is able to borrow is determined in the Comptroller contract. Most notably we can see the collateralFactor and oraclePrice:
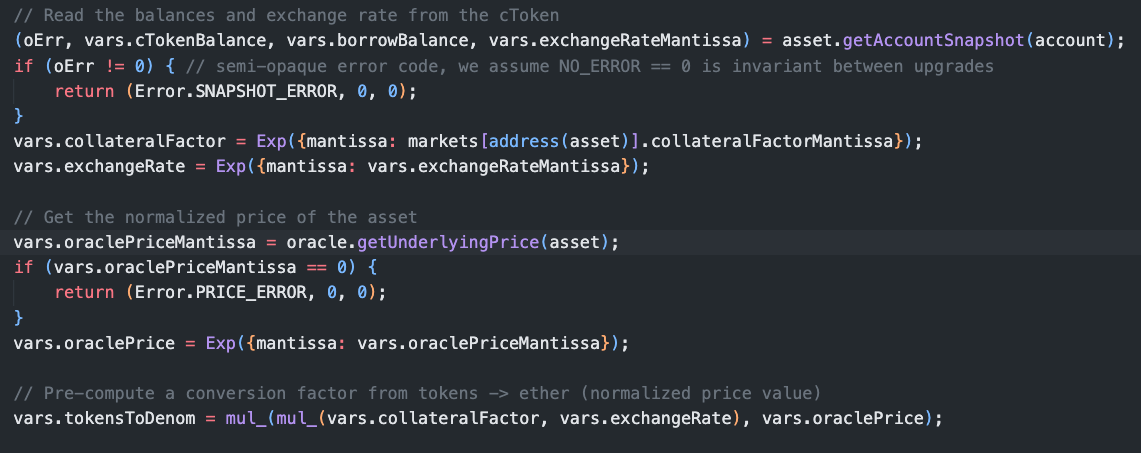
- The collateral factor for lplvGLP is 80, meaning the most a user can borrow is 80% of the value of their deposited plvGLP. Through the donate function, the attacker increased the oraclePrice value of their plvGLP by 1.83 times.
- This allows the attacker to drain more funds than they put into the system. Under normal circumstances, for example, if a user deposited $1,000 worth of plvGLP they should only be allowed to borrow $800 worth of other assets.
- The attacker has however inflated the initial $1,000 worth of plvGLP by a factor of 1.83. This means their borrowing power is now 80% of $1,830 or $1,464 of borrowing power for every $1,000 worth of plvGLP deposited.
- However, all of the debt acquired from this trade is under A. So A transfers the lplvGLP tokens now worth 1.83 times their value to B.
- B uses the lplvGLP tokens to drain liquidity from the other l-token contracts on the platform.
- B then transfers enough tokens back to A to cover their incurred debt and repay their flashloan.
About SourceHat
SourceHat has quickly grown to have one of the most experienced and well-equipped smart contract auditing teams in the industry. Our team has conducted 1800+ solidity smart contract audits covering all major project types and protocols, securing a total of over $50 billion U.S. dollars in on-chain value!
Our firm is well-reputed in the community and is trusted as a top smart contract auditing company for the review of solidity code, no matter how complex. Our team of experienced solidity smart contract auditors performs audits for tokens, NFTs, crowdsales, marketplaces, gambling games, financial protocols, and more!
Contact us today to get a free quote for a smart contract audit of your project!
What is a SourceHat Audit?
Typically, a smart contract audit is a comprehensive review process designed to discover logical errors, security vulnerabilities, and optimization opportunities within code. A SourceHat Audit takes this a step further by verifying economic logic to ensure the stability of smart contracts and highlighting privileged functionality to create a report that is easy to understand for developers and community members alike.
How Do I Interpret the Findings?
Each of our Findings will be labeled with a Severity level. We always recommend the team resolve High, Medium, and Low severity findings prior to deploying the code to the mainnet. Here is a breakdown on what each Severity level means for the project:
- High severity indicates that the issue puts a large number of users' funds at risk and has a high probability of exploitation, or the smart contract contains serious logical issues which can prevent the code from operating as intended.
- Medium severity issues are those which place at least some users' funds at risk and has a medium to high probability of exploitation.
- Low severity issues have a relatively minor risk association; these issues have a low probability of occurring or may have a minimal impact.
- Informational issues pose no immediate risk, but inform the project team of opportunities for gas optimizations and following smart contract security best practices.
